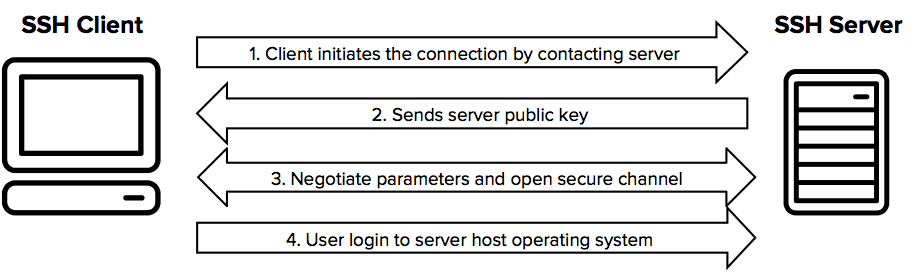
SSH: Your Gateway to Remote Access
SSH, or Secure Shell, is a powerful tool that allows you to securely connect to remote computers and execute commands as if you were sitting right in front of them. It's a cornerstone of system administration, development, and even personal computing.
Why Use SSH?
- Security: SSH encrypts all communication between your computer and the remote server, protecting your data from eavesdropping.
- Remote Access: Manage servers, run scripts, and access files from anywhere with an internet connection.
- Automation: Automate tasks on remote servers using scripting languages like Bash or Python.
- Collaboration: Share access to servers with colleagues or team members securely.
Getting Started with SSH
Install SSH: Most modern operating systems come with SSH pre-installed. If not, you can easily install it using your package manager. For example, on Ubuntu:
sudo apt update sudo apt install openssh-clientGenerate SSH Keys: SSH keys are used for authentication. You can generate a key pair using the
ssh-keygencommand:ssh-keygen -t rsa -b 4096This will create two files:
id_rsa(private key) andid_rsa.pub(public key). Keep the private key secure, and share the public key with the remote server.Connect to a Remote Server: Use the
sshcommand to connect to the server:ssh username@server_ip_addressReplace
usernamewith your username on the remote server andserver_ip_addresswith the server's IP address. You may be prompted for your password or asked to provide your private key passphrase.
Example: Running a Command on a Remote Server
ssh username@server_ip_address "ls -l /home/username"
This command will list the contents of the /home/username directory on the remote server.
Beyond the Basics
SSH offers a wide range of features and options. Here are a few to explore:
- Port Forwarding: Create tunnels to access services on the remote server through a different port.
- SSH Tunneling: Securely access local resources from a remote server.
- SSH Multiplexing: Establish a single SSH connection and use it for multiple sessions.
Conclusion
SSH is an essential tool for anyone working with remote systems. Its security, flexibility, and ease of use make it a valuable asset for system administrators, developers, and anyone who needs to access remote resources.